AI-Powered Cyberattacks: How Hackers are Using ChatGPT in 2025

AI-Powered Cyberattacks: How Hackers are Using ChatGPT Introduction Imagine receiving an email from your boss, except it’s not really them. ...
Read more
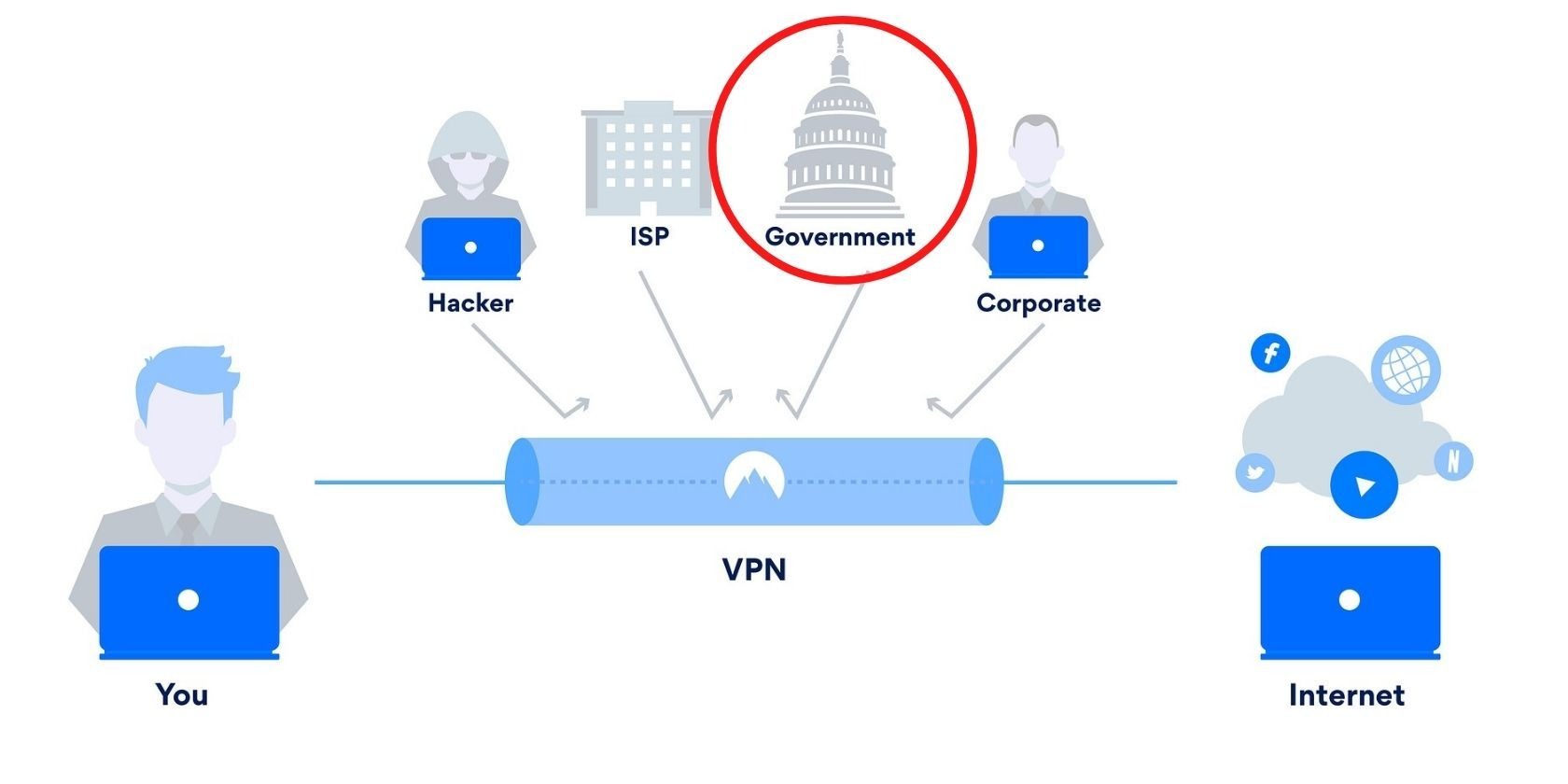
VPNs vs. Proxies vs. Tor: Which One Should You Use in 2025?

Selecting the right tool for safeguarding your digital footprint has become essential because VPNs vs. Proxies vs. Tor: online privacy ...
Read more
The Dark Web Survival Guide: How to Browse Safely with a VPN in 2025

The Dark Web Survival Guide is an unsearchable section of the internet because it escapes both Google and other popular ...
Read more
The 7 Most Dangerous Cyber Threats in 2025 (And How to Stop Them)

The 7 Most Dangerous Cyber Threats INTRODUCTION New cyber threats emerge at an unprecedented rate because 2025 will introduce more ...
Read more
Best No-Log VPNs in 2025: Who Really Keeps Your Data Private?

Using a no-log VPN has become indispensable due to widespread online surveillance, data breaches, and invasive tracking, which flourish in ...
Read more
How to Protect Your Smart Home Devices from Hackers

Protect Your Smart Home Devices INTRODUCTION Devices in smart homes which include voice assistants and Protect smart home devices, together ...
Read more
How to Choose the Right VPN for Your Needs

How to Choose the Right VPN for Your Needs, ExpressVPN and NordVPN remain two of the best VPN services overall. These providers ...
Read more
Cybersecurity Tips for Small Businesses in 2025
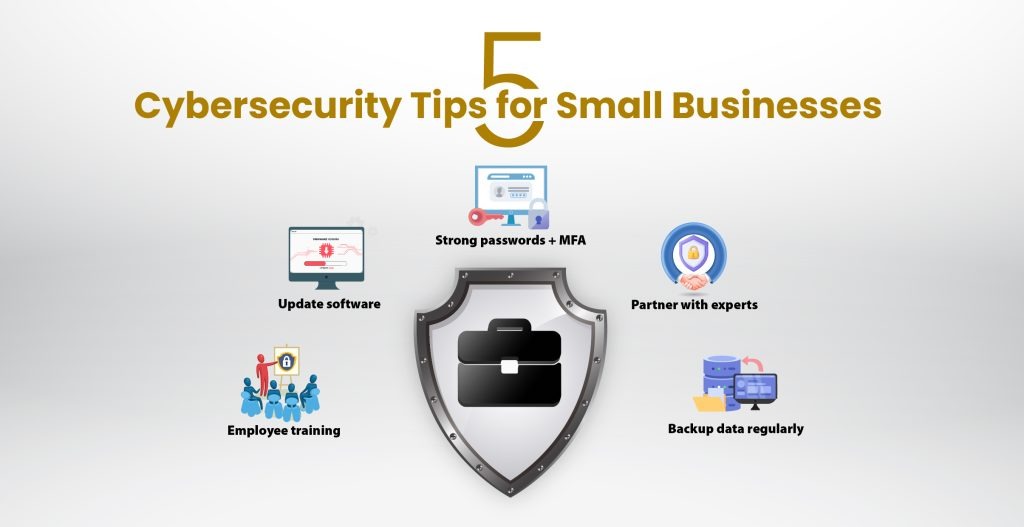
Cybersecurity Tips for Small Businesses INTRODUCTION Modern business operations in the digital sphere have made cybersecurity tips for small businesses ...
Read more