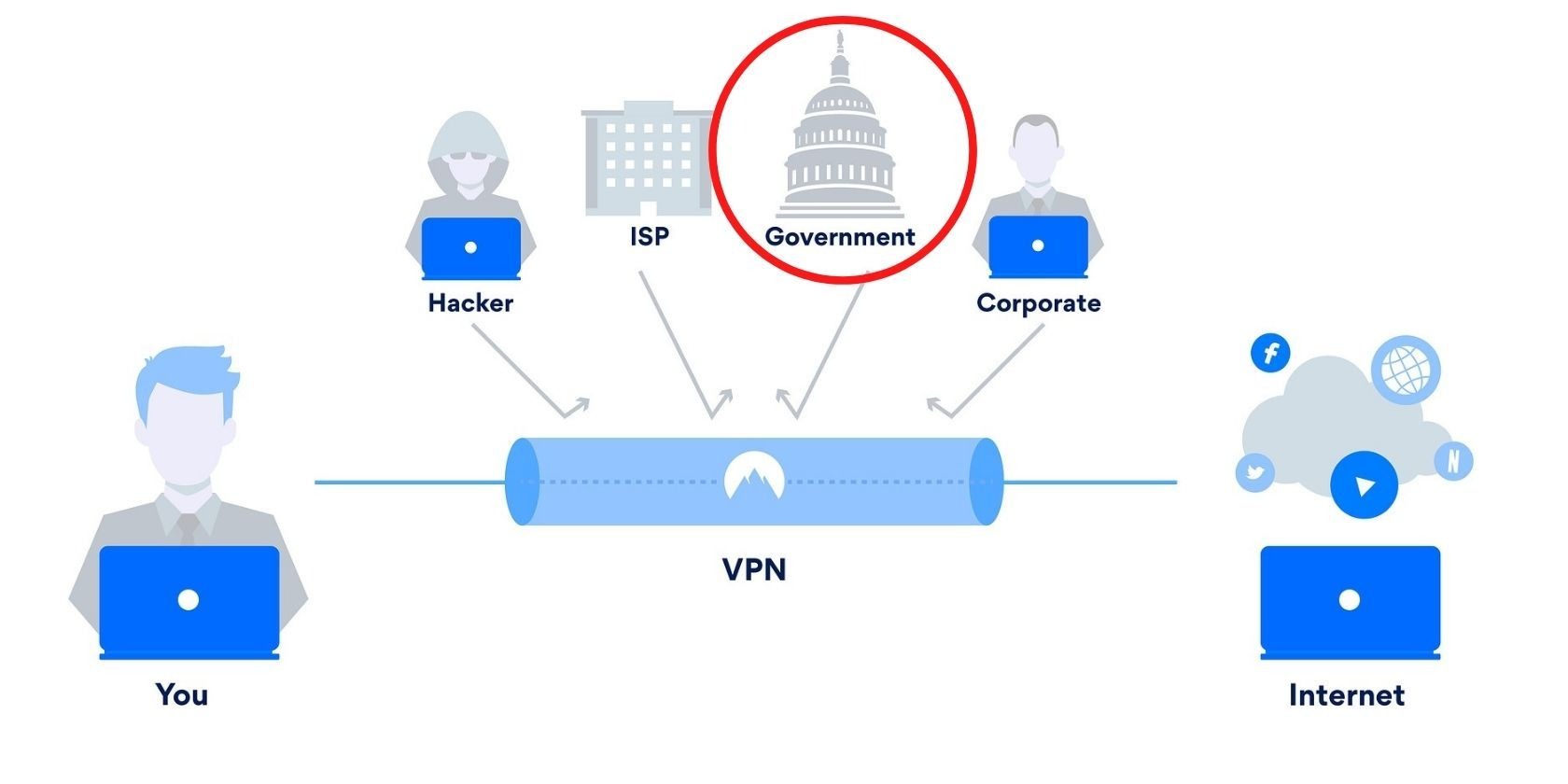
Digital privacy faces persistent threats in modern times, so virtual private networks (VPNs) have become a standard choice for numerous internet users. Can a VPN protect you from government? Different national governments are developing their surveillance capabilities into advanced levels, which involve data collection techniques and hacking tools. The question arises whether VPN services will successfully shield users from state surveillance during the year 2025. No straightforward answer exists regarding this matter. Your VPN privacy stands strong based on diverse elements that include both technological specifications and legal frameworks and the way VPNs are operated by their users. Let’s break it down.
How Government Surveillance Works in 2025
Before assessing VPNs, we need to understand modern surveillance tactics:
1. Mass Data Collection
Governments (especially the Five Eyes alliance) routinely collect internet traffic through:
- Internet Service Providers (ISPs): They log user activity and hand over data when legally compelled.
- Deep Packet Inspection (DPI): Advanced systems analyze internet traffic in real time, even detecting VPN use.
- Backdoors in Tech Companies: Laws like the CLOUD Act force companies to share user data with authorities.
2. Advanced Tracking Methods
Device Fingerprinting: Governments (and hackers) can track you even if you use a VPN by analyzing your browser, hardware, and behavior. Using machine learning, AI systems can detect suspicious online activities, which diminishes the capability of remaining anonymous. National Security Agency intelligence personnel exploit unidentified programming vulnerabilities as a method to bypass encryption limits. Digital privacy faces persistent threats in modern times, so Virtual Private Networks Can a VPN Protect You from government
3. Legal Pressure on VPN Providers
Some countries (China, Russia, and Iran) ban or force VPN companies to log user data. Even in democratic nations, VPNs may comply with subpoenas.
How VPNs Protect You (And Where They Fall Short)
What VPNs Do Well
Encrypt Your Internet Traffic
The secure tunnel in a Digital privacy faces persistent threats in modern times, so virtual private networks (VPNs) allow your device to connect to the internet safely so ISPs and hackers find it hard to monitor your activities. Your Internet Service Provider completely monitors all your internet activities when you lack VPN protection. When you use a VPN, they can only detect ciphered information being sent to the VPN server. Hide Your IP Address Your real IP (which reveals your location) is replaced with the VPN server’s IP. This helps bypass geo-restrictions and prevents basic tracking. Digital privacy faces persistent threats in modern times, so can a Virtual Private Networks (VPN) Protect You from government
Bypass Censorship
In countries like China or Iran, VPNs help access blocked sites (though governments actively block VPN protocols).

Where VPNs Fail Against Government Surveillance
If the VPN Keeps Logs
- Some VPNs secretly store user activity. If authorities demand logs, your privacy is compromised.
Example: In 2020, a free VPN (SuperVPN) exposed millions of user logs due to poor security.
IF the Government Blocks VPNs
- Countries like China and Russia use DPI to detect and block VPN traffic. Only obfuscated VPNs (like NordVPN’s “Obfuscated Servers”) can bypass this.
If You’re a High-Profile Target
If a government is specifically monitoring you, a VPN alone won’t stop them. They might use:
- Malware (like Pegasus spyware) to infect your device.
- Traffic correlation attacks (matching your online activity timing with VPN server logs).
IF You Don’t Use Other Privacy Tools
A VPN doesn’t hide your identity from Google, Facebook, or cookies.
For full protection, you need:
- Tor (for anonymity)
- Encrypted messaging (Signal, Session)
- Anti-fingerprinting browsers (Brave, Firefox with resist Fingerprinting)
Will a VPN Protect You in 2025? It depends.
| Scenario | Does a VPN Help? | Additional Steps Needed |
| General Privacy from Mass Surveillance | Yes | Use a no-logs VPN (ProtonVPN, Mullvad) |
| Avoiding ISP Tracking | Yes | Combine with HTTPS & encrypted DNS |
| Bypassing Censorship (China, Iran, etc.) | Sometimes | Use obfuscated VPNs or Tor |
| Hiding from Targeted Government Spying | No | Use Tor + Tails OS + burner devices |
| Preventing Data Leaks from Apps | No | Use privacy-focused apps (Signal, Proton Mail) |
How to Maximize Protection in 2025
If you’re serious about privacy:
Choose the Right VPN
- No-Logs Policy: Pick providers like Mullvador IVPN (audited and proven).
- Obfuscation helps bypass VPN blocks in restrictive countries.
- WireGuard Protocol: Faster and more secure than OpenVPN.
Combine with Tor
- For maximum anonymity, use Tor over VPN (but it slows down speed).
Use Privacy-Focused Devices & OS
- GrapheneOS (Android), Tails OS, or Qubes OSresist tracking better than Windows/macOS.
Avoid Leaking Data Elsewhere
- Disable WebRTC (it can expose your real IP).
- Use Firefox with uBlock Origin to block trackers.
Assume You’re Being Watched
- If you’re a journalist or activist, go beyond VPNs—use burner phones, encrypted emails, and anonymous payment methods.
Pros and Cons-Comprehensive Analysis
Advantages (Pros) of Using a Pros-and-Cons List
Structured Decision-Making
- Provides a clear, organised way to evaluate choices.
- Reduces impulsive decisions by forcing thoughtful analysis.
Identifies Strengths & Weaknesses
- Highlight benefits (why an option is good) and drawbacks (potential risks).
- Helps prioritise factors that matter most (e.g., cost, time, impact).
Encourages Objectivity
- Minimises emotional bias by focusing on facts.
- Useful for business, personal life, and critical decisions.
Improves Risk Assessment
- Reveals hidden challenges before committing.
- Allows contingency planning for potential downsides.
Facilitates Comparisons
- Useful when choosing between multiple options (e.g., job offers, investments).
- Can assign weights to different pros/cons for better clarity.
Boosts Confidence in Choices
- Reduces regret by ensuring all angles are considered.
- Serves as a reference if outcomes need reevaluation.
Disadvantages (Cons) of Using a Pros-and-Cons List
Oversimplifies Complex Issues
- Some decisions involve intangible factors (e.g., ethics, emotions) that don’t fit neatly into lists.
- May ignore long-term consequences in favour of short-term gains.
Subjectivity & Bias
- Personal preferences can influence how pros/cons are weighted.
- Two people might create very different lists for the same decision.
Analysis Paralysis
- Too many pros/cons can make decisions overwhelming.
- Leads to delays when quick action is needed.
Lack of Nuance
- Doesn’t account for “grey areas” where pros and cons interact (e.g., a “con” might be mitigated by a “pro”).
- May not consider changing circumstances (e.g., market shifts).
Time-Consuming
- Not practical for minor, everyday choices (e.g., “What to eat for lunch?”).
- Requires effort to research and validate each point.
Overconfidence in the List
- People may assume the list is foolproof, ignoring intuition or new information.
- Some pros/cons may be based on assumptions rather than facts.
Example: Detailed Pros & Cons of Social Media
Pros of Social Media
Global Connectivity
- Instant communication with friends, family, and professionals worldwide.
- Breaks geographical barriers for networking and collaboration.
Information & Awareness
- News spreads rapidly (useful for emergencies, activism, and education).
- Access to diverse perspectives and learning resources.
Business & Career Growth
- Marketing platform for entrepreneurs and freelancers.
- Job opportunities via LinkedIn, remote work communities, etc.
Entertainment & Creativity
- Platforms like YouTube, TikTok, and Instagram foster creativity.
- Memes, trends, and viral content provide entertainment.
Support Communities
- Mental health groups, niche hobbies, and advocacy movements thrive online.
- Crowdfunding (e.g., GoFundMe) helps people in need.
Cons of Social Media
Mental Health Risks
- Linked to anxiety, depression, and low self-esteem (comparison culture).
- Cyberbullying and harassment are prevalent.
Privacy & Security Issues
- Data mining, identity theft, and scams.
- Facial recognition and location tracking raise surveillance concerns.
Misinformation & Polarization
- Fake news spreads faster than fact-checked information.
- Algorithms create echo chambers, increasing societal divides.
Addiction & Time Wasting
- Designed to be habit-forming, reducing productivity.
- Doom scrolling (compulsive consumption of negative content).
Superficial Relationships
- Online interactions often lack depth compared to real-life connections.
- “Cancel culture” can lead to disproportionate public shaming.
Conclusion
Average users who choose quality VPN services receive protection against surveillance activities along with prevention of tracking from Internet Service Providers and minor censorship attempts. People in dangerous positions, such as whistleblowers and activists, will need security beyond VPN usage. Government efforts toward improved intelligence require privacy tools to develop accordingly. The most effective defence strategy for 2025 requires multiple layers of security protection. You will need a VPN alongside the Tor network, followed by encrypted apps as well as tools that stop fingerprint detection. People who prioritise their privacy need to use more security measures in addition to using a VPN since a VPN must be understood and adapted along with these other protective measures. Your digital privacy depends entirely on the weakest element within your security framework between today and the current digital era.