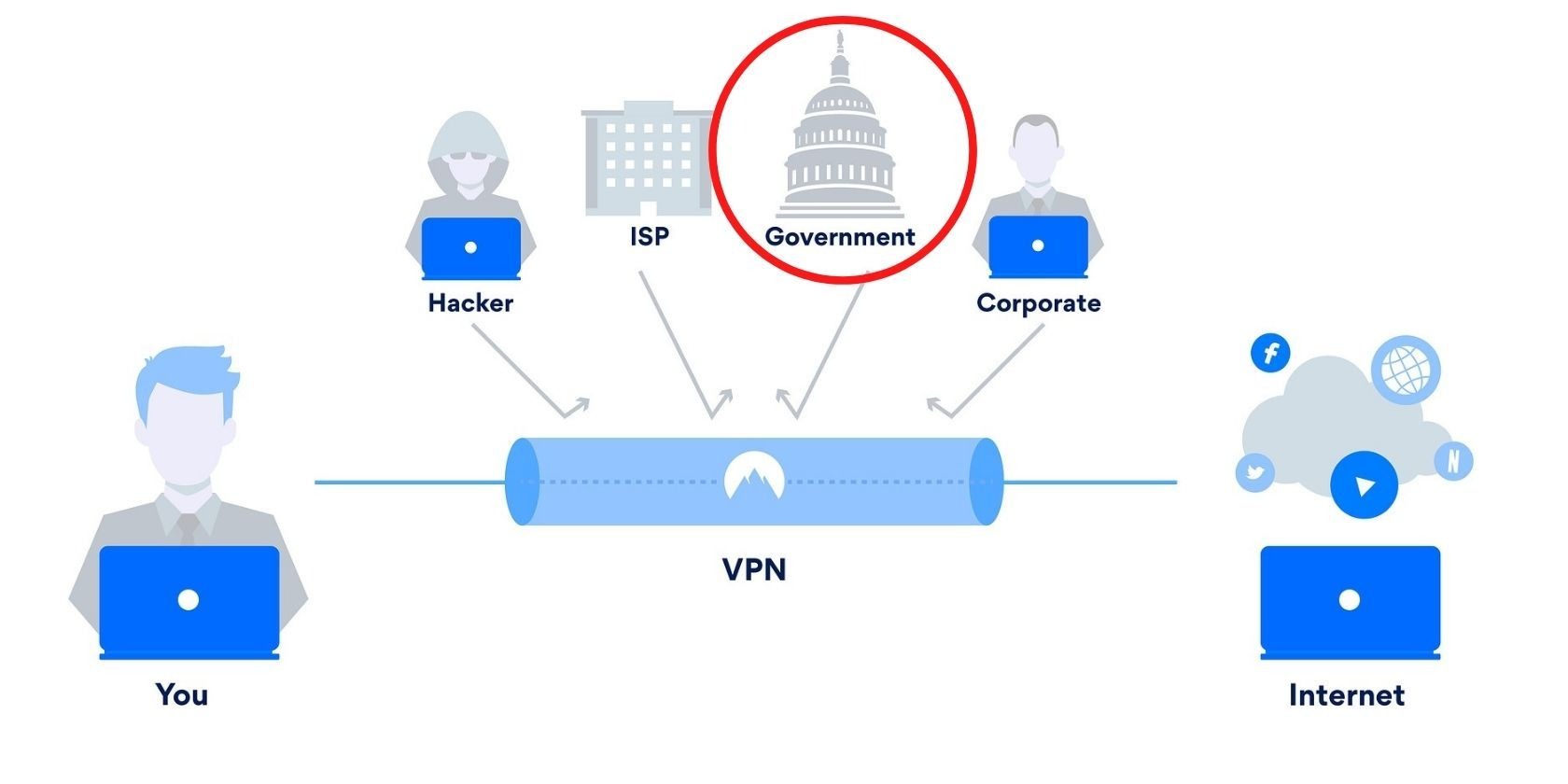
Zero Trust vs. VPNs: What Will Dominate CyberSecurity in 2025?

Fans of secure remote access preferred Virtual Private Networks (VPNs) as the standard security Zero Trust vs. VPNs: solutions during ...
Read more
AI-Powered Cyberattacks: How Hackers are Using ChatGPT in 2025

Imagine receiving an email from your boss, except it’s not really them. The tone, AI-Powered Cyberattacks: even the subtle quirks ...
Read more
VPNs vs. Proxies vs. Tor: Which One Should You Use in 2025?

Selecting the right tool for safeguarding your digital footprint has become essential because VPNs vs. Proxies vs. Tor: online privacy ...
Read more
The Dark Web Survival Guide: How to Browse Safely with a VPN in 2025

The Dark Web Survival Guide is an unsearchable section of the internet because it escapes both Google and other popular ...
Read more
The 7 Most Dangerous Cyber Threats in 2025 (And How to Stop Them)

New cyber threats emerge at an unprecedented rate because 2025 will introduce more 7 Most Dangerous Cyber Threats. Attacks orchestrated ...
Read more
Best No-Log VPNs in 2025: Who Really Keeps Your Data Private?

Using a no-log VPN has become indispensable due to widespread online surveillance, data breaches, and invasive tracking, which flourish in ...
Read more
How to Protect Your Smart Home Devices from Hackers

Devices in smart homes which include voice assistants and Protect smart home devices, together with smart thermostats and door locks, ...
Read more