The Dark Web Survival Guide is an unsearchable section of the internet because it escapes both Google and other popular search engine catalogues. The dark web typically appears to people through illicit activities, including black market operations and hacking forums, along with cybercriminal activities, yet it maintains genuine applications related to privacy communication, anonymity, whistleblowing, and censorship evasion. To browse the dark web safely, you need to take proper safety measures before stepping into its digital minefield. Dark web traffic always faces monitoring from law enforcement agencies, together with hackers and scammers, which makes complete anonymity necessary for users. The necessary component for dark web access is a VPN, which stands for Virtual Private Network.
In this guide, we’ll break down:
What the dark web really is (and isn’t)
Why a VPN is non-negotiable for dark web browsing
Step-by-step instructions for safe access in 2025
Common dangers and how to avoid them
Understanding the Dark Web vs. Deep Web
1.1 The Layers of the Internet
- Surface Web (10% of the internet): Publicly accessible sites (Google, Facebook, news sites).
- Deep Web (~90% of the internet): Password-protected or private databases (bank accounts, medical records).
- Dark Web (a small fraction): Hidden sites requiring special browsers like Tor (The Onion Router).
1.2 Who Uses the Dark Web?
- Journalists & Whistleblowers: Secure communication (e.g., SecureDrop).
- Privacy Advocates: Avoiding government surveillance.
- Cybercriminals: Illegal marketplaces (drugs, stolen data).
Fun Fact: The dark web was originally developed by the U.S. Navy for secure communication!
Why You Need a VPN for the Dark Web in 2025
2.1 How Tor Works (And Its Weaknesses)
Tor anonymises your traffic by routing it through multiple encrypted nodes. However:
- Entry/Exit Nodes Can Be Monitored: ISPs and hackers can detect Tor usage.
- IP Leaks: Malware or misconfigurations can expose your real IP.
2.2 How a VPN Adds an Extra Layer of Security
A VPN encrypts your connection before it reaches Tor, masking your IP from your ISP and preventing exit node snooping.
Best VPNs for Dark Web Access (2025)
|
VPN |
Key Features |
|
NordVPN |
Double VPN + Onion Over VPN servers |
|
ProtonVPN |
Swiss-based, strict no-logs policy |
|
Mullvad |
Anonymous sign-up (no email needed) |

Step-by-Step Guide to Safe Dark Web Browsing in 2025
3.1 Before You Start: Essential Precautions
Use a secure OS: Tails OS (runs from USB, leaves no traces).
Disable JavaScript: Prevents exploits in Tor Browser.
Never Use Personal Info: Assume everything is monitored.
3.2 Setting Up Your VPN + Tor (The Safest Method)
- Connect to a VPN (choose a server in a privacy-friendly country).
- Download Tor Browser (only from the official site: org).
- Enable “Safest” Security Settings (blocks scripts and risky content).
Biggest Dangers & How to Avoid Them
4.1 Common Dark Web Threats
- Scams & Fake Markets: Exit scams (sellers take money and disappear).
- Malware: keyloggers and ransomware hidden in downloads.
- Honeypots: Fake sites set up by law enforcement.
4.2 Red Flags to Watch For
“Too good to be true” deals (e.g., $10 for a Netflix lifetime account).
Unencrypted (.onion) sites asking for logins.
Links from unverified forums.
Case Study: In 2023, the FBI shut down Genesis Market, the Dark Web Survival Guide marketplace selling stolen credentials. Many users were tracked via VPN leaks.
Pros of Browsing the Dark Web with a VPN
1. Enhanced Privacy & Anonymity
- VPN + Tor = Maximum Security
- A VPN hides your IP from your ISP, while Tor encrypts your traffic through multiple layers.
- Prevents exit node surveillance (where hackers or governments monitor Tor traffic).
2. Bypass Censorship & Surveillance
- Useful in oppressive regimes where governments block websites (e.g., journalists in China and Iran).
- Whistleblowers can leak information securely (e.g., via SecureDrop).
3. Access to Unfiltered Information
- Research & Archives: Some libraries and databases are only available on The Dark Web Survival Guide.
- Privacy Tools: Secure email services (ProtonMail), encrypted forums, and uncensored news.
4. Avoid Tracking & Data Harvesting
- No Google, Facebook, or ad tracking your activity.
- Ideal for activists, hackers (ethical), and privacy-conscious users.
Cons of Browsing the Dark Web with a VPN
1. Legal Risks
- Even with a VPN, some activities are illegal (e.g., buying drugs, stolen data).
- Law enforcement monitors dark web markets (e.g., the Silk Road takedown).
2. Scams & Malware Threats
- Fake markets (exit scams where sellers disappear after payment).
- Infected downloads (ransomware, spyware hidden in files).
3. Slow Speeds & Unreliable Connections
- Tor + VPN = slower browsing (data passes through multiple encrypted nodes).
- Some sites are offline or unreliable (frequent takedowns).
4. Psychological & Ethical Concerns
- Disturbing content (illegal markets, hacking forums, extremist groups).
- Ethical dilemmas (accidentally stumbling upon criminal activity).
Critical Considerations Before Accessing the Dark Web
|
Factor |
With VPN |
Without VPN |
|
Anonymity |
High (ISP can’t see Tor usage) |
Low (ISP detects Tor) |
|
Security |
Encrypted before Tor |
Vulnerable at the entry node |
|
Risk of Exposure |
Low (if VPN is no-log) |
High (IP leaks are possible) |
|
Speed |
Slower (double encryption) |
Slightly faster |
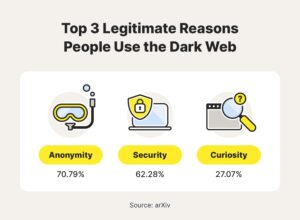
Final Verdict: Should You Use the Dark Web with a VPN?
Yes, if you…
Need absolute privacy (journalists, activists).
We are researching censored information.
Use only legal, ethical services (SecureDrop, privacy forums).
No, if you…
Want to access illegal content (high risk of scams, malware, legal trouble).
Aren’t tech-savvy (misconfigurations can expose you).
Just curious without a real need (not worth the risks).
Best Safe Alternatives
- For privacy: Use Tor over VPN + Tails OS.
- For anonymity: ProtonMail, Signal, Mullvad VPN.
- For research: legitimate deep web databases (academic journals, private archives).
Final Checklist for Safe Browsing
- Always use a reliable VPN before Tor.
- Stick to legal activities (e.g., privacy forums, secure email).
- Never download files or enable scripts.
- Assume every interaction is monitored.
Conclusion: Is the Dark Web Worth the Risk?
The dark web exists as a double threat, which provides privacy protection but at the same time serves as a base for unlawful operations. Tor operates as a powerful tool for whistleblowers, journalists, and users who need to avoid censorship, but companies expose users to severe risks such as fraud schemes, malware, and police investigations. Everyone who wants to navigate the dark web needs to follow minimum security guidelines, which include combining a VPN with Tor, never revealing personal details, and staying away from criminal content. However, for most users, the dangers outweigh the benefits. There is no valid reason for most people to access the dark web because of the established risks involved. Keeping yourself informed and following safety precautions must be your primary security priority.